After using this Facebook Hacker Pro 2.8.9 Activation Key mostly Facebook users enables to get extra hacking knowledge easily. It has totally main functions. Then press the button “Recover Password” this Facebook Hacker Pro 2.8.9 Activation Code program will enable you to crack FB passwords of your choice.
Facebook Hacker Pro 2.8.9 Crack With Activation Key Free Download
Facebook Hacker Pro Activation for you You can easily hack any Facebook ID with help. You can also cut any Facebook ID password. If you forget the Facebook id password always Then, you want to recover it by hacking the password. It is an advance, best, and newest tool for picking different Facebook accounts. You can also secure your Facebook ID password by this
Facebook Hacker Pro Crack is powerful software that is fabulous those individuals; they usually use Facebook and desire to hack the Facebook reports of others who are targeted. People can cut the Facebook stories that will differ use that is making of computer software efficiently. It offers incredible features being high; the client can gain quick and free of cost. The Facebook Hacker professional is the elegant computer plus it provides an amount that is right of to the designer, creator, designer, and therefore the client to reduce the complexity that is hacking.
The Facebook hacker pro is the version that is latest than several other variations. This hacking computer software is utilized whenever the customer that is a concern that is commonly anyone who is cheating him. Your individual has consequently confused and tries to comprehend the facts. Your individual chooses to hack the account of the average person
Facebook Hacker Pro
By using the Facebook hacker pro key, the mostly Facebook account user capable of gaining more account knowledge that is hacking. The Facebook hacker pro has entirely effortless hacking. After doing a bit of function that is fundamental, the tab is pressed by you“recover a password.” This Facebook hacker computer programs shall competent to an individual establishing the Facebook password according to the select option. The person that is an average hack, anyone, Facebook ID quickly and in the tiny schedule after doing these actions.
Facebook Hacker Pro also fulfills the majority of connected with a need that is crucial of particular. We recognize that some Facebook IDs can hack quickly, and some are hard, and then you have to take the time that is a lot. It is also competent to regain lost that is whole of ID this Facebook hacker computer PC software that is professional quite simple and directly takes incredibly less time. The individual can download it from the CX crack`s site that is the internet.
Hacking Facebook / Facebook Hacker is hugely searched, and hot topics the Internet like Gmail hacker. I have ready a list that is detailed of pirates could hack someone’s Facebook account easily in a few moments, and how could we prevent a similar. Being an FB white hat hacker, we frequently get these appropriate concern from many people
People think these Questions 😛
- Will there be any Facebook cracker device?
- Where may I get FB hacking computer software?
- Is there any facebook password finder that is free?
- To your best of my knowledge, there is no such device; you don’t think it is anywhere and yeah without finishing a survey that they indeed are providing free hack tool however you cannot
- download it if you google it, you’d find many internet sites claim.
- Even after finishing a scholarly study, you won’t get anything in conclusion.
- Of making money. Don’t waste your valued time in such searching tool is the hack.
- The technique that is most that work some these methods is PHISHING that enables anyone without any or small technical knowledge to hack a
- Facebook account’s password effortlessly in a few moments
- Have a look at this phishing a-z guide to understanding more about PHISHING!
- Read Ways to Recover Hacked Facebook Account
- hacking facebook account easily | facebook hacker
- Some associated with the practices listed below are not merely relevant to FB but to all or any daily utilized internet websites like Google, Twitter, Yahoo, etc.
- You won’t be vulnerable to hacking in case you understand how works that are cutting
- Please don’t use these processes for sinister purposes.
- Get all of the hacks that is right that is secret your inbox. Subscribe to us now!
Ten means to hack someone’s FB account | Prevention and Safety Measures - Phishing is the technique that is most that are common for hacking FB passwords.
- Numerous individuals become a victim of Phishing page due to its layout that is the trustworthy plus.
- In simple words,
- Phishing is a way of creating a duplicate copy of a reputed website’s web page to steal a user’s password or other information that is the charge that is delicate details.
- Inside our subject,
- producing a page which entirely seems like Facebook login page but in an URL that is fakebook.com that is different or faecbook.com or any URL which pretends to be legit.
- When a user lands on such a page that is typical she or he might believe that is Facebook, that is the real web page and asking them to provide their password.
- John is a programmer; he produces an FB login page with scripts that are few enable him getting the password and username information.
- John place this login that is fake in https://www.facebouk.com/make-money-online-tricks.
- Peter is a buddy that is close to. John delivers a message to Peter “Hey Peter, I came across an easy method to online make cash effectively,
- you need to take a look that is great this https://www.facebouk.com/make-money-online-tricks”.
- Peter demands the link and sees a Facebook login page.
- As usual, Peter comes into his username and password of FB.
Precisely how will you protect yourself from FB phishing?
- Hackers can achieve you in several means like email, personal messages, FB messages, Website ads, etc.
- Clicking any links from these messages would lead you to a Facebook login web page.
- You need to notice only one thing that may be URL because nobody can spoof/
- use Facebook URL except when you’re able to find some XSS zero vulnerabilities
- but that’s very rare whenever you see an FB login page time.
- What’s the URL you see in the browser address bar?
- Is that https://www.facebook.com/ (Trailing slash is essential since it is the separator that is chrome that is
- Google differentiate domain and subdomain. Read the examples which are below
- Also, start to see the below examples of phishing pages.
Some phishing that is super is ideal are given below.
- Facebook Phishing that is a perfect web page
- Facebook Phishing Page – Note the misleading URL
- All the people that are social suspect this site (snapshot provided above) since there is https prefix with the green color secure icon and no blunder in www.facebook.com. But this is a phishing web page, just how?
- Note the URL correctly. It is https://www.facebook.com.infoknown.com, so www.facebook.com is a subdomain of infoknown.com. Google Chrome does not distinguish the domain and sub-domain, unlike Firefox do.
- SSL Certificates (HTTPS) could be had from many vendors; few vendors give SSL Certificate for Free for one year. It’s maybe not a deal that is big a novice to create phishing that is ideal such as this. Therefore be aware of it.
- Phishing Some Body’s Facebook Account Password
Facebook Phishing Page – Note the misleading URL.
This is an FB that is phishing that is normal some modification in the word Facebook. - Read How to generate Blogspot weblog and earnings that are created Adsense
2 Social Engineering
This is undoubtedly the second technique that is most that are typical of Facebook reports. This procedure should come under Hacking’s since no knowledge is with this method. I will be listing this approach under hacking to make sure the list of most techniques that are typical for FB account hacking within their particular purchase. Social engineering is merely a procedure of gathering information about someone whose account you need to hack. Information like date of birth, their mobile quantity, their boyfriend/girlfriend’s mobile number, nickname, mother’s title, original destination, etc.
How did Social Engineering work?
- Facebook-Social-Engineering-Security-Question
- FB-Social-Engineering-Security-Question
- Many websites have a password that is the option that is the typical Security Question. Most protection that is typical would be, “What is the nickname?” , “What is your grade that is the score that is 10th,
- “What is your native place?” or any custom questions defined by the user. Acquiring this given information from individuals that are respective let us back to their account. Facebook too provides security concern as password recovery choice. Therefore if anyone become familiar with the precise answer from it, they might cut your account using forgot password choice.
Security Question doesn’t permit you to obtain into others FB account quickly. But establishing a password that is poor promptly enable any certainly one of friends and household to hack into your account. What’s a password that is bad this scenario? A password that can easily be guessed by a person that is a thirdly called password that is poor. Listed here are some the most passwords which can be normal tend to use within Facebook.
- Mobile Number
- Boy Friend’s / Girl Friend’s Name – Many regarding the lovers?
- Boy Friend and Girl Friend Name Combination
- Nickname / Name and Date of Birth Conjunction
- Boy Friend’s / Girl Friend’s Mobile Number – Many for the lovers?
- Bike Number
- Unused / Old Mobile Number
- Pet Name
- Closest Person name(can be friends too)
- Now be honest and comment right here if you are one among individuals who’ve any one of essential passwords that are typically above. Don’t forget to change your password
- before you comment?
Features of the Facebook Hacker Pro Crack:-
- This might be another exciting feature, which is its function that is anonymous to your footprints.
- The patient can employ this regarding the screen PC, laptop computer, and nearly any other device.
- It is a method that is hugely is pure all the social those who are social have to hack the reports.
- By the Facebook hacker pro, the patient can access the victim`s account quickly in some second.
- No need for ant capability that is technical by using this software application.
- It supports all operating systems are Android.
- Individuals that participate in almost any felids can effortlessly employ this extremely.
- Someone might hack various other media that are social because concerning the aid of the
Screenshot:-
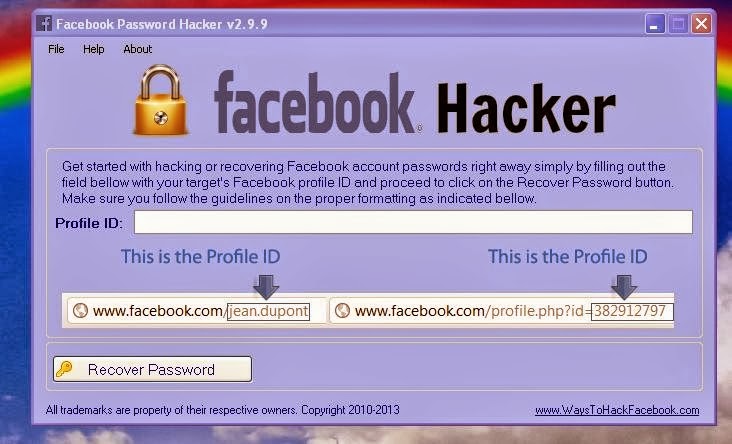
How to Crack?
- First Download Cracked File From Below
- Extract it and Force to Run
- Click on Installed Setup File
- Wait for installation
- When all is Done Then Click on Generate Serial Number
- Copy this and Paste
- After that Click on Active
- Wait for Process
- Enjoy
Related
Pass Revelator is the only website in the computer world to offer the best solutions to recover a Facebook password, to find a Twitter password, for GMail, Yahoo ! or MSN if you've lost or forgotten it. And of course it helps you get back a Wi-Fi combination from the network. Through this website, you will find your IDs in minutes.
It also provides you the best service to recover an Instagram password! You could find all your pictures again!
Working with the major players and publishers in the computer market, Pass Revelator's software are synonymous of security and education. Over the years, our unique solutions have built a solid reputation from their users thus demonstrating the skills they have internationally.
Access every Instagram account password with this software
You can download it totally FREE. Learn how to break into your Facebook account for free. You can get someone's GMail IDs by using our security fail system. You just need to provide the email address to connect to the Twitter messenger you want to enter, and after a few clicks, our system will automatically display the hidden key for you right on your screen. To enter into a MSN, Hotmail, Outlook or Live account with our recovery service has never been easier. To view someone's Facebook private life within minutes is now available on the Internet. The person will not realize that his GMail account has been unlocked.
Why do hackers want your WiFi password?
You need to download any of our decryptor software to secure your Twitter account again. Just enter the email address you want to view and you can get someone's data. You do not need to complete any online survey to have access nor to pay. No, you can have it totally free of charge. You may wonder why we need to unsecure a FB profile?
There are several reasons for a person to do this. In order to keep an eye on their children, the parents may want to know what they are doing on the Internet. A boyfriend or girlfriend wishes to know what their loved one is doing behind their back. A husband may want to know whether his wife is loyal or not. Thinking of using a FB account? No worries, there aren't many ways you can do this.
Here is the free Facebook decipher application available on our website.
How to find MSN, Outlook and Hotmail complex combinations?
It's not depending on how complex and how long their key is. Our achievement is to use an algorithm method to bypass the security of the database, which means we can succeed in logging into an email address. When successful, you will be notified by a text message appearing on the screen. Copy and paste it on the website and also enter their username or email address. You will then be able to connect to the Twitter profile.
It is a good security practice to use a complex password when you create an MSN, Live, Outlook or Hotmail account. However, you are lost if you have not used it for a while. If you have returned to your online messenger, you find that you can't access your webmail.
Fortunately, there is one solution, Password Revelator.
Just use the tool and let our automated system unlock the security of the online messenger for you, it's as easy as that! We use various powerful algorithms in the application which enables it to get access to any account.
Hack your GMail account to check your security!
This is the answer to the previous question. Is any of it really possible? Yes it is, who knows maybe your account is under the control of a hacker? Thanks to GMail Password Breaker, you have certainly heard about of how unsafe Google service is with a few politicians having had their passwords hacked. You may also have seen that it allows you to synchronize status updates.
Which method should be used you might ask? It's much simpler. You simply enter in our software the email of the profile you want to access and all the questions you might have are solved right away, as you gain access to the other person's life, and are able to see what they think of you.
Also, you may be interested to hack a Wifi password security key WEP/WPA2 in order to test your security network. We provide you with our wireless hacker detector for free.
Our software, allows you to use all the wifi hotspots you want in just a few minutes and all for free. So, you gain in two ways. First, the software is free and secondly, you will stay online without paying anything.
Our WLAN Hacker promises and guarantees the resolving of any wireless technology network without even the slightest problem, it makes the whole process enjoyable and fun. The number of WiFi hacks you can do with it is amazing.
For more info on security concerns when using our online access point, please read the paragraph that follows.
You don't need to hire a professional and you don't need any obscure computer knowledge at all. Our application also works on an Android phone or tablet. You are so lucky you got here early that you don't even need to buy this program, because for a limited time we're giving it for free! You want to check and to understand why hack Yahoo! account, we will bring you an answer! If you want to learn how to log in to Yahoo messenger or crack your webmail fast and effectively, just follow the directions strictly. Once you've typed the email, then you have achieved about 90% of your work to enter into Yahoo account for real.
Because data protection is essential to everyone, creating a Facebook password shouldn't be done in a few minutes as it can be easily hacked. When registering on a website, the dilemma is always the same: should I choose a secure Twitter password, difficult to remember or an easy one, at my own risk? Unfortunately, often users still look for the second solution, with 'asteriks' for the password such as '123456' or 'password'.
You should know that to avoid hacks, you should have a sufficiently long GMail password as the capacity of hackers to hack a password depends first on its length. The software they use automatically tests all possible combinations. Each additional character significantly increases the time it takes to 'crack' an Instagram password.
A string of eight to twelve characters is a good compromise between security and ease of memorization. A password using a variety of characters: hacker software is also programmed to test all dictionary words, a large number of first names, and of course all calendar dates (forget your grandmother's birthday). It is therefore necessary to use a variety of characters such as uppercase, lowercase, numbers, and various punctuation characters...
A unique Outlook password: Each web site/subscription used by the user must have a different access key. This avoids putting all of his eggs in one basket.
A WiFi password is not created directly, but must be derived from a phrase that ensures a certain level of complexity while remaining memorable.
For example, retain the first letter(s) of each word composing a sentence. Then, each one has to bring his personal touch by incorporating a few capital letters (one letter out of two, or of three for example), and numbers (to replace some letter by figures whose typography is similar is very effective).
Example: Let's use the following sentence: 'The eye sees nothing if the mind is distracted': By choosing to use the first letter of each word, a capital letter every two letters, and replacements of the O and E by 0 and 3, we obtain: 0nVrSl'33D. Such a Yahoo password would take about 500 million years to be decrypted by a standard computer. The use of phonetics. When pronouncing a sentence, each sound will generate one of the characters of the Facebook password.
Naturally, not all sentences are suitable, but once the choice is made, the memorization will be easy. Example: Based on the sentence 'I bought three eggs and two comics this morning.' Always with a capital letter every two letters, get: gHt3E98BdCeMPT1.
Use a common structure to manage a variety of Facebook passwords.
It is possible to create a common core, complete with a second part specific to each service (Facebook, Twitter etc.).
Example of common trunk (fixed): the title of his favorite film. Example of second part (variable): the name of his favorite singer.
Example: If you like 'Star Wars' and your favorite singer is Michael Jackson, the password will be (always with a capital letter for two letters and replacing the E with a 3): LaGuD33t-MiJa. We voluntarily took the first two letters of each word in order to arrive at a sufficient length.
Choose a 'classic' password, then shift each letter of a key to the right.
Example: starting with the first name James, we get (always with a capital letter for two letters) KOZ, EUmZiNE.
Once the Instagram password has been chosen, do not hesitate to go and test it on a password verifier that informs of its security level and gives an estimate of the time needed to hack it. You will then quickly perceive the weakness of many combinations that you consider inviolable.
Also for Facebook, once created, the Facebook password must be protected in order to not get hacked. To do this, avoid keeping it in a computer file that malicious souls will take care to analyze. Physical preservation is also to be avoided.
We forget the post-it placed under the computer screen! They allow the access codes of all the sites used to be stored, in the same database, accessible by a single password. You will have the opportunity to create very safe combinations, without having to retain them.
Free Facebook Password Hacker
While debates about privacy on the Internet generally concern the giants of the web and the carelessness of young users, it is one thing that must not be forgotten: hacking. And as in real life with a burglary, you usually do not think about it enough before you are concerned. Yet it is mathematical: the more we store information online on Facebook, Instagram... the more we use different services and supports, and the more vulnerable we are.
More than 15000 web attacks were recorded by computers security companies. Even if these figures come from a company that lives in security (and thus insecurity) IT, they deserve to be taken into GMail account. Especially as our data are more and more personal and critical (social networks).
So what to do?
If you ask a specialist, the first answer might be: PEBKAC? The acronym of 'Problem Exists Between Keyboard And Chair', in the language of not IT expert: the problem lies between the keyboard and the chair.
Still not understood?
The problem often comes from the user, not the tool. Preventing rather than curing. This is not a phrase you like to hear, but there is often a background of truth behind it. Because the first thing you can do to avoid Twitter stolen data is to use computer tools with caution. And learn to master them.
While you have the best antivirus, it will eventually get overtaken if you do not take your precautions. Thus, the basic principles, such as not visiting unknown sites and little referenced without protection, not to click on a link without knowing what it is, or to update its computer and its antivirus are the first to respect. In the same vein, never respond to strange and unlikely e-mail strings, never give your password to anyone (person) or never leave your session open on a public computer.
The targets of hackers are often people who do not respect these few rules. However, even with these basic precautions, there is always a risk. There are a few tips to improve the security of your WiFi data online.
Free Password Finder Download
Internet users spend more time on Facebook, communicating sensitive and valuable personal information, and hackers have found the vein. The Instagram social networks themselves and their users are to take more measures to protect themselves from organized crime on the Internet. The progression of attacks by hackers and other 'spammers' aimed at social sites like Facebook, Twitter or Instagram, has reached a 'worrying' level, according to the computer security company.
There are different types of hacking via Twitter networks:
First the spam that arrives on your Facebook or Twitter accounts.
Social networks are quite well protected against this type of piracy, because to be able to send a spam, the hacker must be 'friend' of the victim. Very visible, this type of attack is used by computer security companies to communicate on the subject, but this is only the tip of the iceberg.
Then there are the more subtle false ads, which return directly to malicious sites, whose code allows to hack the GMail password of the victim.
Finally, there are also fake Facebook groups, which offers a link to a page of 'phishing', by which an uninformed user, believing to address a site of trust, will enter his personal data.
Your personal data are then sold between 10 and 15 dollars. The data of the user of Facebook or Yahoo, once recovered, can be used directly by the hacker, or resold between 10 and 15 dollars on a specialized forum 30 seconds later. With a login (password) and an email address, it is easy for him to get more information about his victim.
According to an analysis carried out, more than half of Internet users (56%) use only one password on all the sites on which they are registered. The hacker can therefore peel off the mails from his victim, in order to obtain additional information (physical address, Facebook data, pictures, phones, etc.) and then steal it.
A number of databanks are now introducing physical security systems, with the creation of Facebook passwords generated for a single use, but overall it is difficult to ensure that the personal data provided by social network is not used against them by a malicious user. People have to understand that we must not say everything about the Internet.
With more and more professional hackers, the threat increases in both quantity and quality. The figure makes you dizzy: 2 million viruses are in circulation every day. The phenomenon of 'ransomware' as WannaCry illustrated the new danger that falls on our computers as well as our smartphones. We must add the good old phishing by e-mail. However, just a few precautions to avoid the inconvenience of losing his data, his memories of holidays or access to his accounts on social networks. Here are the 'must-do' to ensure a minimum of cybersecurity on PC, Mac and smartphones.
The e-mail box is always the first vector of infection. Reminder sting: Do not open an attachment or link sent by an unknown address even if the email looks like an official email such as Tax or Social Security. It is also necessary to renew the passwords every 6 months by avoiding easy to find information by cross-checking your public profiles such as birthdates or landline numbers.
In the same logic, it is necessary in absolute terms not to trust any free wi-fi network. The great innovation of hackers is to create fake wireless Internet networks to suck your passwords or bank details but also access your mailboxes.
With democratized cloud solutions (iCloud, Google Drive...), it's easy to save your files online. The most fearful about their personal data will opt for an external hard drive disconnected from the web. Be careful not to make simple copies because ransomware like Wannacry can encrypt and block them. It must go through a complete backup software.
Free Facebook Password Finder Activation Code Free
Doped with artificial intelligence, malware and other viruses learn to get around antivirus sometimes faster than they are updated. This is why comprehensive protection solutions exist with a dozen technological layers: firewalls, connection filters, e-mail filtering... It will take a little investment to avoid further problems.
A technology expert that is working with us has managed to hack a Facebook account thanks to the former phone number of its owner. Facebook and Instagram encourages its users to fill in their phone number to increase the security of their account.
What if it actually opens the door for pirates?
Facebook Password Finder
Thanks to an old phone number reassigned to a new person, hackers could access the Facebook account of users who linked this number to their account, according to a technology expert.
Since the arrival of the artificial intelligence, the programs can directly interact with the vulnerabilities of the databases of the servers and thus extract passwords from Snapchat accounts. Sophisticated algorithms allow to elaborate a neurological structure that can be able to reproduce the human mentality and thus decode all Snapchat passwords.
A simple SMS to hack an account
Free Password Finder Software
The social network allows any user to recover his forgotten password by receiving a sms containing a code to enter to be able to access his account again. A handy system when you have a memory hole. But according to our hacker expert, it would also allow hackers to access users' personal data. It will be easy to hack Instagram account.
The danger? The reassigned phone numbers. He simply did a search on the social network by searching for the user who associated this number to his account and then asked for a forgotten password. He then followed the protocol that allowed him to access the account of his victim.
Free Facebook Password Finder Activation Code Windows 7
A hacking technique potentially very profitable. For users who want to learn how to hack a Facebook account, this solution, all in all simple enough, the computer specialist ensures that hackers could earn a lot of money.
Two-factor authentication has become essential over the years to secure online accounts that contain more and more personal data. Unsurprisingly, many online services offer it to their users. If it is advisable to activate it to be able to sleep on both ears, it should not be too much for it. Security researchers have shown how they can appropriate any online account by hacking this protection mechanism.
The process is known; to enable two-step verification, the user must provide a phone number in addition to the username and password already entered when creating a GMail account, for example. Once this number is verified, the user can activate SMS two-factor authentication on said account. The measure prevents an attacker who has the username and password of the account from accessing the account from his workstation. Indeed, past the first curtain of protection (the couple username and password), the cybercriminal must provide a code sent by the online service on the phone number associated with the account.
The measure is also useful to 'recover' his account in the case of loss of details of the first shield. Most online services then offer an SMS account recovery procedure. (Concretely, it is question that the online service sends text information recovery account to the number linked to the latter.) This state of affairs assumes that a third party who knows the phone number linked to the account can mingle with the distance. How to hack Facebook? By exploiting the flaws of the SS7 protocol used for signaling on telecommunication networks.